What is Sepsis ransomware
Sepsis – is a ransomware virus, which means it may cause a lot of headache to any user. In case you are reading this article just because of curiosity – we strongly recommend you not to open any shady spam emails with attachments and keep a proper anti-virus application on your computer. The ransomware can be distributed by hacking through an unprotected RDP configuration, email spam and malicious attachments, fraudulent downloads, exploits, web injections, fake updates, repackaged and infected installers. Sepsis ransomware is able to use encryption on all important files, then ask for money to decrypt. In fact, no one can tell for sure if they would decrypt these files. Most of cyber criminals ignore their victims, some of them even have no idea how to decrypt encrypted data. That’s why if your computer is infected with Sepsis ransomware, you should not pay for decryption of your files. Still, you can remove Sepsis ransomware and decrypt .Sepsis files without paying anything.
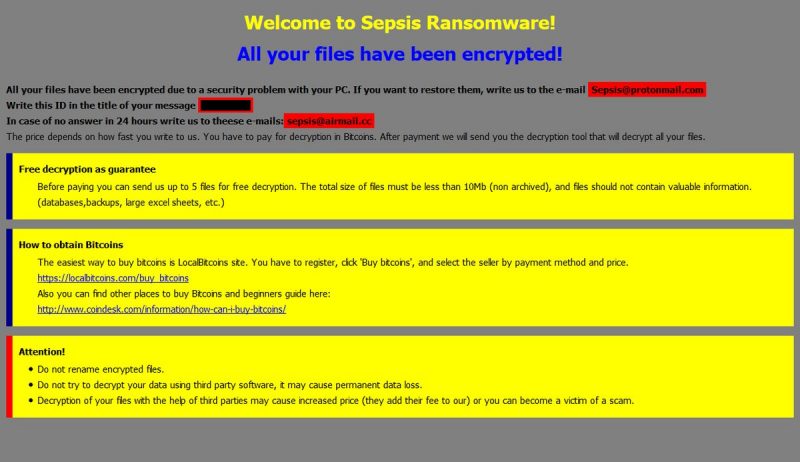
The way this ransomware works is quite simple – first of all, Sepsis breaks through your system, then starts encrypting procedure with AES + RSA-2048 encryption algorithm. Sepsis ransomware adds .[Sepsis@protonmail.com].SEPSIS extension to the name of all the encrypted files. For example, photo.jpeg file turns into photo.jpeg.[Sepsis@protonmail.com].SEPSIS file. Once the encryption is done, the virus drops Info.hta file and pop-up window with a ransom note:
Welcome to Sepsis Ransomware!
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail Sepsis@protonmail.com
Write this ID in the title of your message ***
In case of no answer in 24 hours write us to theese e-mails: sepsis@airmail.cc
The price depends on how fast you write to us. You have to pay for decryption in Bitcoins. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 10Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click ‘Buy bitcoins’, and select the seller by payment method and price.
https://locabitcoins.com/buy bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk.com/information/how-can-i-buy-bitcoins/
Attention!
• Do not rename encrypted files.
• Do not try to decrypt your data using third party software, it may cause permanent data loss.
• Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
There are two solutions of this problem. First is to use special Removal Tool. Removal Tools delete all instances of malware by few clicks and help user to save time. Or you can use Manual Removal Guide, but you should know that it might be very difficult to remove Sepsis ransomware manually without specialist’s help.
Sepsis Removal Guide
- Download Sepsis Removal Tool.
- Remove Sepsis from Windows (7, 8, 8.1, Vista, XP, 10) or Mac OS (Run system in Safe Mode).
- How to Decrypt Sepsis files.
- How to restore system to previous “condition”.
- How to protect PC from future infections.
How to remove Sepsis ransomware automatically:
This removal tool can help you to get rid of this nasty virus and clean up your system. In case you need a proper and reliable solution, we recommend you to download and try it. This anti-ransomware removal tool is able to detect and remove Sepsis ransomware from your system.
Manual Sepsis Removal Guide
Below is step-by-step instructions to remove Sepsis from Windows and Mac computers. Follow this steps carefully and remove files and folders belonging to Sepsis. First of all, you will need to run system in a Safe Mode. Then find and remove needed files and folders.
Uninstall Sepsis from Windows or Mac
Windows 7/Vista:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Sepsis by using Removal Tool;
- Delete found files;
Windows 8/8.1:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Sepsis by using Removal Tool;
- Delete found files;
Windows 10:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Sepsis by using Removal Tool;
- Delete found files;
Windows XP:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Sepsis by using Removal Tool;
- Delete found files;
Mac OS:
- Restart the computer;
- Press and Hold Shift button, before system will be loaded;
- Release Shift button, when Apple logo appears;
- Find programs or files potentially related to Sepsis by using Removal Tool;
- Delete found files;
How to decrypt Sepsis files
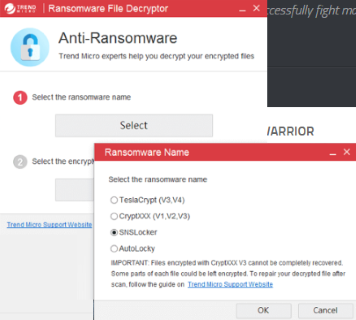
After Sepsis is removed, you want to decrypt your documents and files. There are different decrypting tools, that can help you.
After removing Sepsis, you can try to decrypt Sepsis files. All you need is decrypting tool. There may be a trouble – not all of the files can be decrypted and restored, it depends on ransomware.
One of those programs is Trend Micro Ransomware File Decryptor. This software decrypt a lot of types ransomware file formats, you may try to use in order to decrypt infected files.
How to restore encrypted files
If you can’t remove and decrypt files or just don’t want to use those instructions, you can try to restore system from recovery point by using special tools: Previous Versions, System Restore, Shadow Explorer. You can also try Data Recover Pro application in order to restore your files, give it a try.
Restore data with Stellar Data Recovery
- Download and install Stellar Data Recovery
- Choose drives and folders with your data, then press Scan.
- Select all the files in a folder, then click on Restore button.
- Manage export location. That’s it!
Restore encrypted files using Shadow Explorer
Shadow Explorer – is good software with simple interface, that gives an access to “shadow copies”.
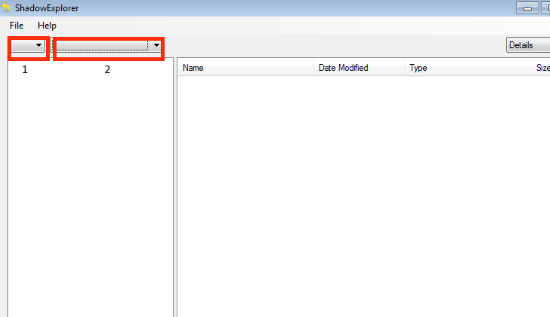
- Run the Shadow Explorer;
- Choose local disk, that contains needed files (sector 1 on picture);
- Choose time period, when files weren’t encrypted (sector 2 on picture);
- Find needed files and folders, after this right-click them and Press Export;
- Choose the export location and check files;
Restore encrypted files using Recuva
There is another program, that can help user to recover encrypted files. And this program is Recuva, software which friendly interface.
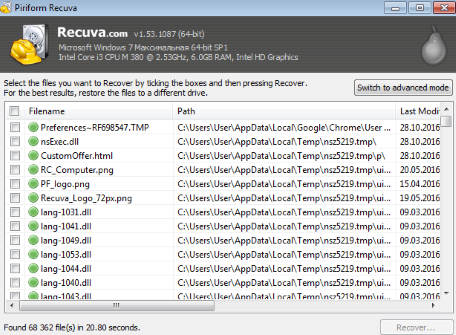
- Run the Recuva;
- Follow instructions and wait until scan process ends;
- Find needed files, mark them and Press Recover button;
How to prevent ransomware infection?
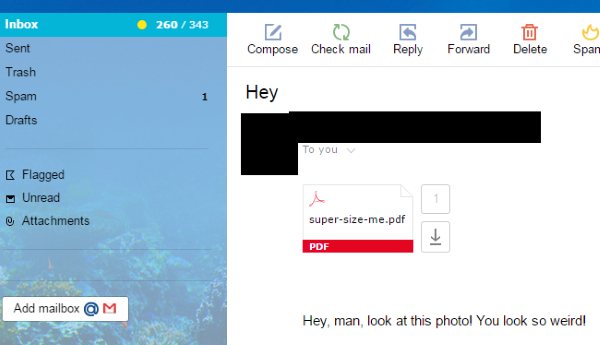 Since Sepsis classified as ransomware, it needs a method to infiltrate into personal computer. And the most usable method is attaching to e-mail with messages, that provocate to open attached document.
Since Sepsis classified as ransomware, it needs a method to infiltrate into personal computer. And the most usable method is attaching to e-mail with messages, that provocate to open attached document.
Be careful while reading e-mail from unknown and suspicious users. Also, you can install various programs, which will stop any actions from suspicious applications, like ransomware. The most popular programs are:
HitmanPro.Alert with CryptoGuard, Malwarebytes Anti-Ransomware and CryptoPrevent. Those programs may detect many known ransomware and some unknown ransomware. It is recommended to use such programs for safety of your personal documents and files in future.

![How to remove Sepsis ransomware and decrypt .[Sepsis@protonmail.com].SEPSIS files](https://malwarewarrior.com/wp-content/uploads/2018/05/mw-sepsis-ransomware.jpg)