What is Troldesh ransomware
Troldesh ransomware – is another malware with popular monetizing scheme. After appearing on computer, Troldesh begin to encrypt files and documents by using special encrypt algorithm. This process eats a lot of resources, so you may notice low PC performance. Encrypted files will get a new name with ransomware email and .xtbl file extension. After all, Troldesh leaves various files to inform user about decryption. At those files, developers offer user to pay 1.5 bitcoins to get a decryptor. But there is a chance, that after payment user may not get a decryptor. This is why we not recommend to pay money, better remove Troldesh ransomware from computer as soon as possible and after this decrypt encrypted .xtbl files.
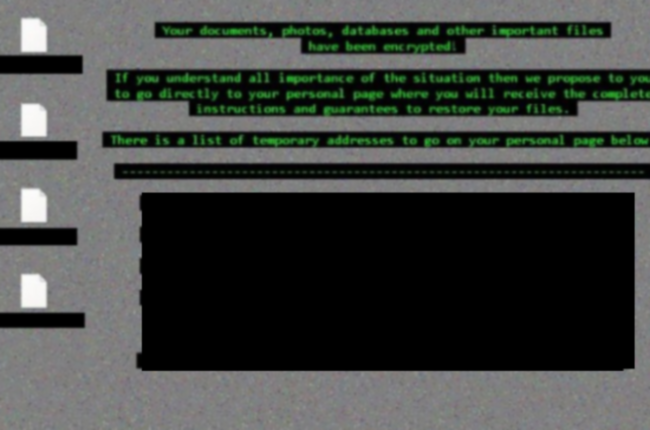
There is a list of file types, which can be affected by Troldesh ransomware:
.sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .odt
There are two solutions of this problem. One is to use special Removal Tool. Removal Tools delete all instances of malware by few clicks and help user to save time. Or you can use Manual Removal Guide. Manual Removal Guides help user to remove malware manually. This method needs time and knowledge at IT sphere.
Troldesh Removal Guide
- Download Troldesh Removal Tool.
- Remove Troldesh from Windows (7, 8, 8.1, Vista, XP, 10) or Mac OS (Run system in Safe Mode).
- How to Decrypt .xtbl files.
- How to restore system to previous “condition”.
- How to protect PC from future infections.
Troldesh Automated Removal Tools:
Use removal tool to uninstall Troldesh. Trial version of Malwarebytesdetects Troldesh ransomware and assists in its removal for FREE.
 |
 |
| Norton by Symantec does not need any advertising. Time-tested product and one of the leaders in anti-virus and anti-malware protection. Read more… | Kaspersky Lab id famous for its newest antivirus technologies. Kaspersky Antivirus and Internet Security are the world top security programs. Read more… |
| Download Norton | Download Kaspersky |
Manual Troldesh Removal Guide
Below is step-by-step instructions to remove Troldesh from Windows and Mac computers. Follow this steps carefully and remove files and folders belonging to Troldesh. First of all, you will need to run system in a Safe Mode. Then find and remove needed files and folders.
Uninstall Troldesh from Windows or Mac
Windows 7/Vista:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Troldesh by using Removal Tool;
- Delete found files;
Windows 8/8.1:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Troldesh by using Removal Tool;
- Delete found files;
Windows 10:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Troldesh by using Removal Tool;
- Delete found files;
Windows XP:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Troldesh by using Removal Tool;
- Delete found files;
Mac OS:
- Restart the computer;
- Press and Hold Shift button, before system will be loaded;
- Release Shift button, when Apple logo appears;
- Find programs or files potentially related to Troldesh by using Removal Tool;
- Delete found files;
How to decrypt .xtbl files
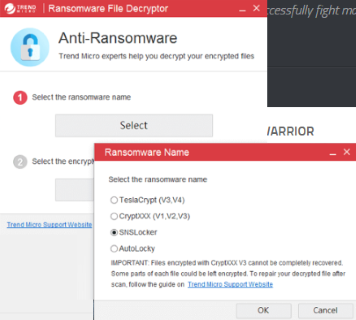
After Troldesh is removed, you want to decrypt your documents and files. There are different decrypting tools, that can help you.
After removing Troldesh, you can try to decrypt xtbl files. All you need is decrypting tool. There may be a trouble – not all files can be decrypted and restored, it is depends on ransomware.
One of those programs is Trend Micro Ransomware File Decryptor. This software decrypt a lot of types ransomware file formats. You don’t even need to find encrypted files, it will do anything by itself. You can download Trend Micro Ransomware File Decryptor here.
How to restore encrypted files
If you can’t remove and decrypt files or just don’t want to use those instructions, you can try to restore system from recovery point by using special tools: Previous Versions, System Restore, Shadow Explorer. Be sure, that you have saved recovery point, otherwise you can’t do anything with some tools.
Restore encrypted files using Shadow Explorer
Shadow Explorer – is good software with simple interface, that gives an access to “shadow copies”.
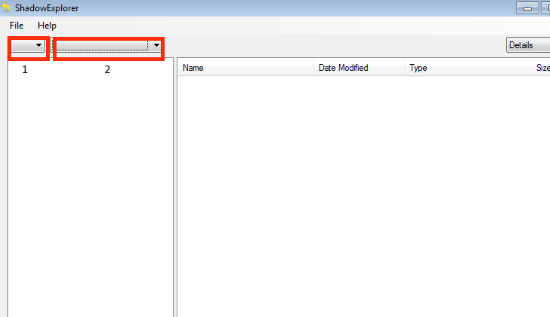
- Run the Shadow Explorer;
- Choose local disk, that contains needed files (sector 1 on picture);
- Choose time period, when files weren’t encrypted (sector 2 on picture);
- Find needed files and folders, after this right-click them and Press Export;
- Choose the export location and check files;
Restore encrypted files using Recuva
There is another program, that can help user to recover encrypted files. And this program is Recuva, software which friendly interface.
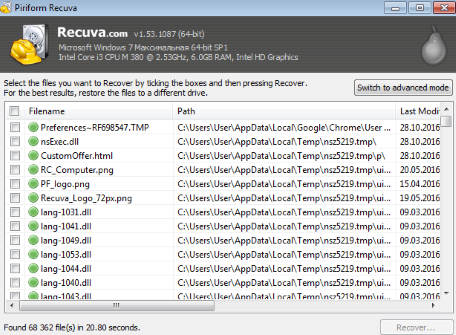
- Run the Recuva;
- Follow instructions and wait until scan process ends;
- Find needed files, mark them and Press Recover button;
How to prevent ransomware infection?
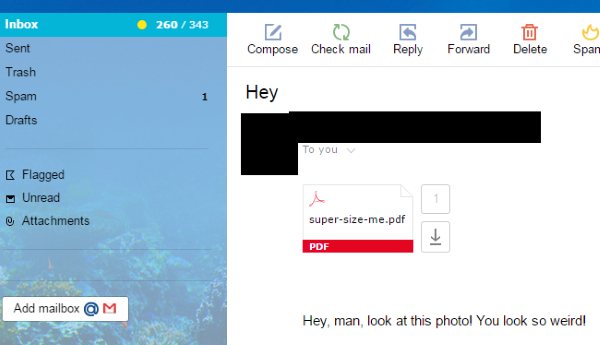 Since Troldesh classified as ransomware, it needs a method to infiltrate into personal computer. And the most usable method is attaching to e-mail with messages, that provocate to open attached document.
Since Troldesh classified as ransomware, it needs a method to infiltrate into personal computer. And the most usable method is attaching to e-mail with messages, that provocate to open attached document.
Be careful while reading e-mail from unknown and suspicious users. Also, you can install various programs, which will stop any actions from suspicious applications, like ransomware. The most popular programs are:
HitmanPro.Alert with CryptoGuard, Malwarebytes Anti-Ransomware and CryptoPrevent. Those programs may detect many known ransomware and some unknown ransomware. It is recommended to use such programs for safety of your personal documents and files in future.

