IRIS Ransomware is a type of malicious software that infects computers by encrypting files on the system and demanding a ransom in exchange for the decryption key. This ransomware typically spreads through phishing emails, malicious websites, or exploit kits.
When IRIS Ransomware infects a computer, it adds a specific file extension to the encrypted files, such as “.iris” or “.locked”. It uses strong encryption algorithms like AES or RSA to encrypt the files, making them inaccessible without the decryption key.
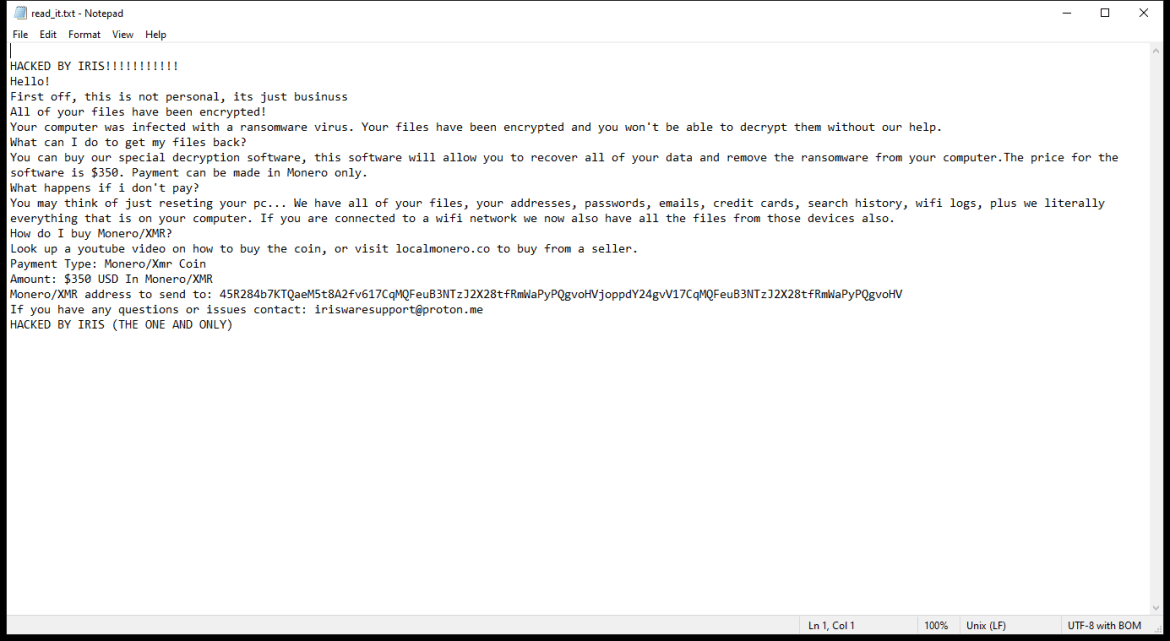
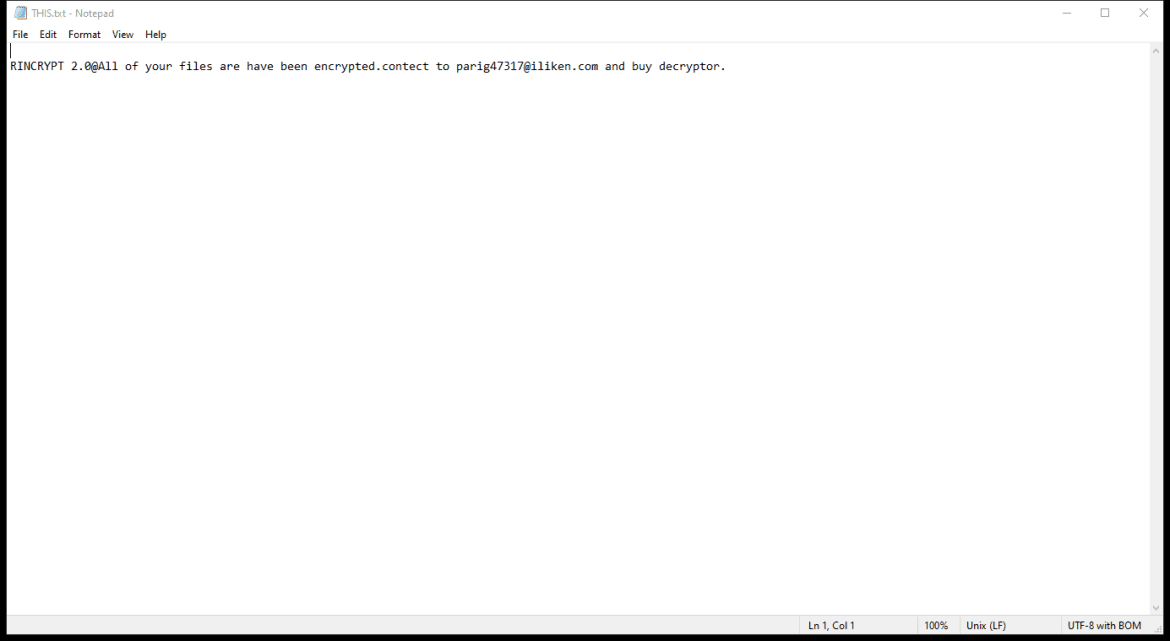
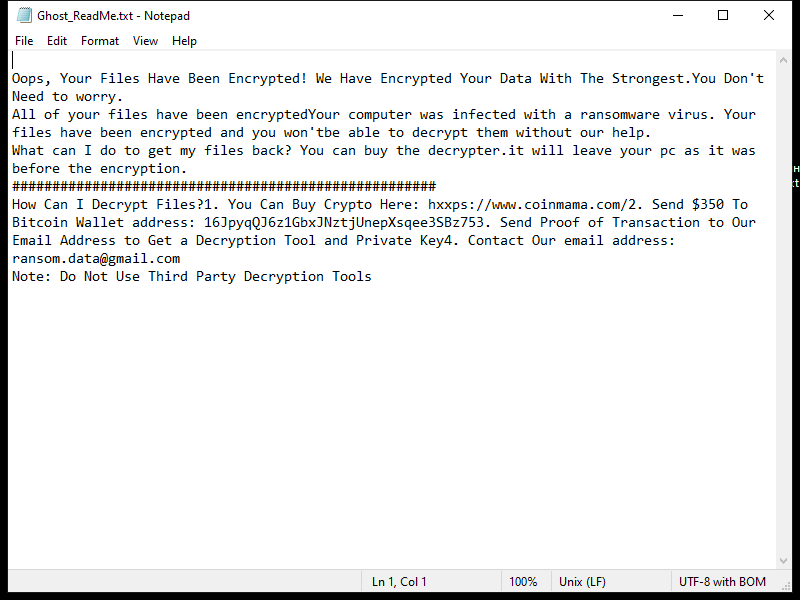
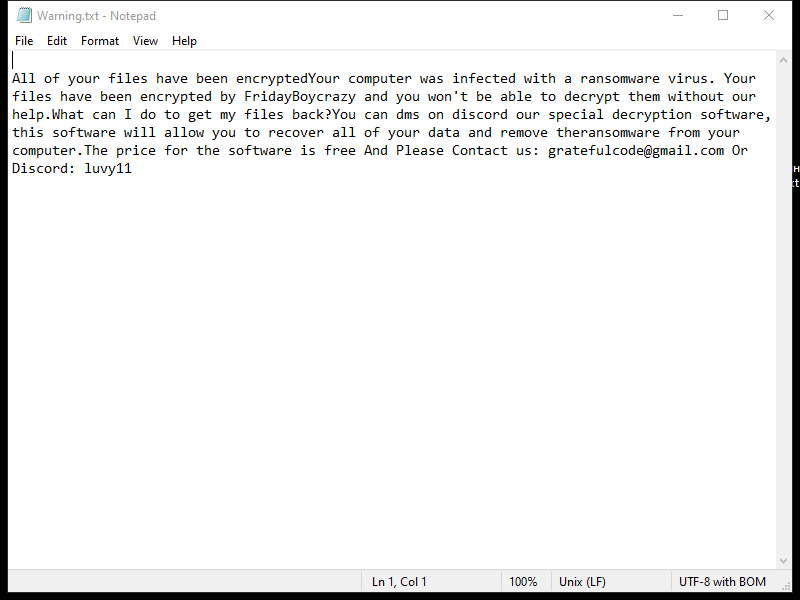
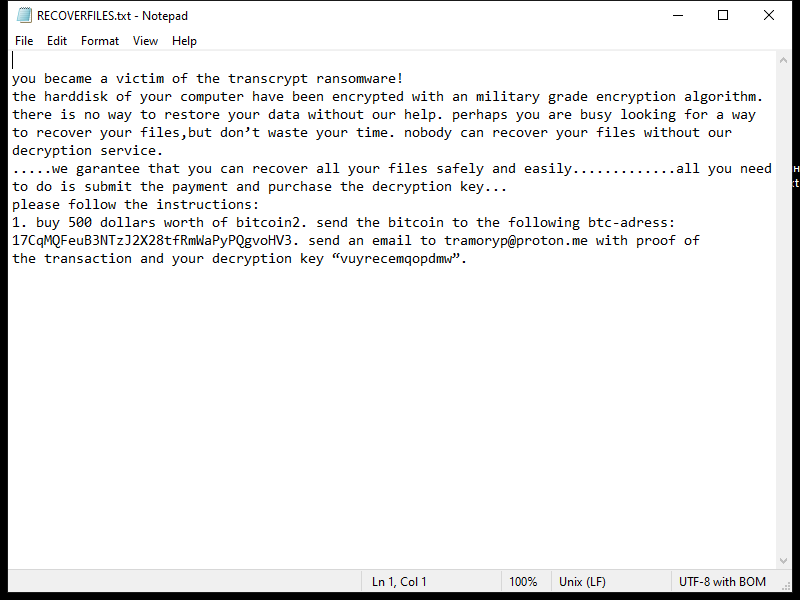
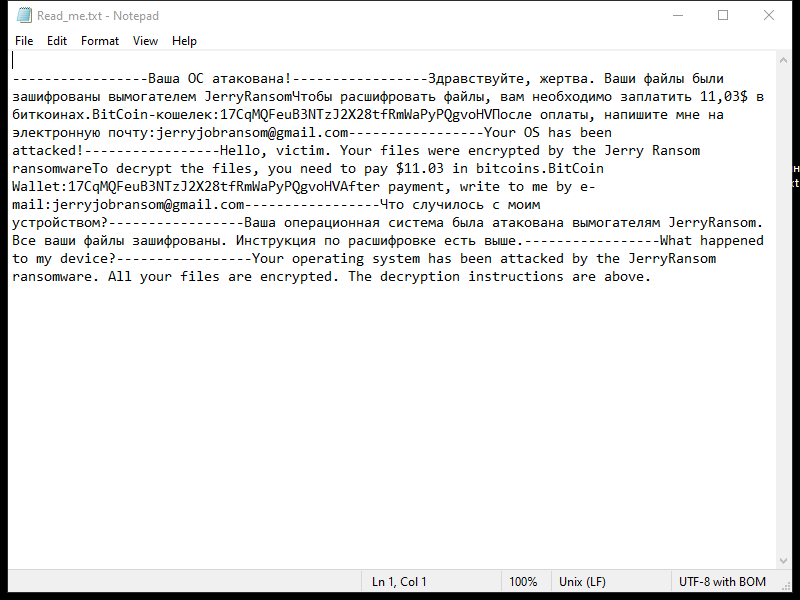
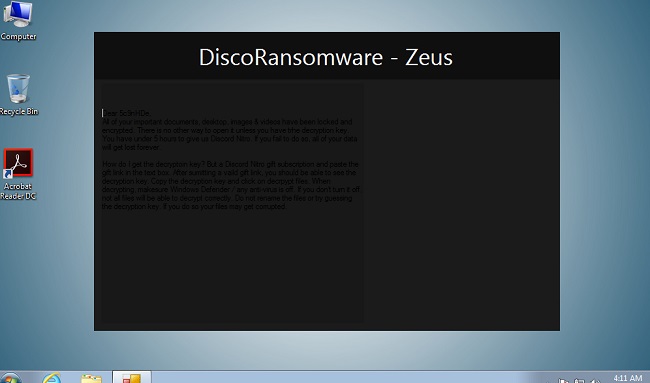
After encrypting the files, IRIS Ransomware creates a ransom note that usually appears as a text file on the desktop or in every folder containing encrypted files. The ransom note provides instructions on how to pay the ransom and obtain the decryption key.
Unfortunately, there are currently no decryption tools available for IRIS Ransomware. However, there are some methods you can try to decrypt your files, such as using third-party data recovery software, restoring from backups, or seeking help from cybersecurity professionals.
Overall, it is important to regularly back up your files, use strong and updated security software, and avoid clicking on suspicious links or downloading attachments from unknown sources to prevent falling victim to ransomware attacks like IRIS.