What is Reco Ransomware
Recently, the STOP cryptovirus family has become very widespread. Reco ransomware is another representative of these malicious creations. Like the old ones, Reco ransomware encrypts user data using a complex, multi-stage algorithm. Some users believe that the virus only changes the extension of these files to .reco, but everything is much more complicated. It is also worth noting that the files become inoperative after such manipulations. That is why you need to remove Reco ransomware and decrypt .reco files.

Cryptovirus is aimed at users who speak English. At least, such a conclusion can be made based on the text of the _readme.txt note that appears in folders with encrypted files. However, recently, it has already spread almost all over the world (Western and Eastern Europe, Latin America, Australia and so on). Below we have posted an image of a scam note and its content:
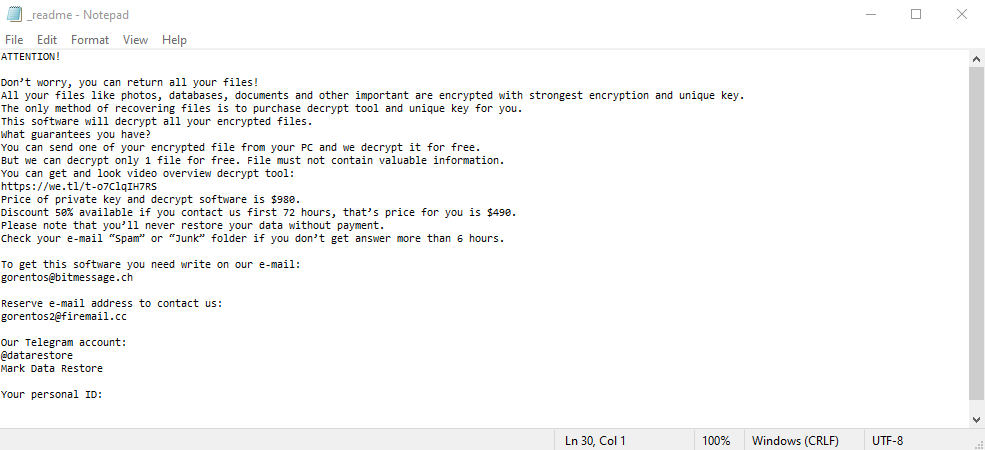
ATTENTION!
Don’t worry my friend, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-oEUEuysYiZ
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
stoneland@firemail.ccReserve e-mail address to contact us:
gorentos@bitmessage.chSupport Telegram account:
@datarestoreYour personal ID:
From time to time, the appearance and content of the notes that cryptoviruses of the STOP family leave are practically unchanged. Attackers demand a ransom of US $ 980, or offer a Reco, according to the rules of which the user can count on a 50% discount if paid in the first 3 days. Of course, you don’t even have to pay a penny. We strongly advise you not to waste your time finding independent solutions. Use our recommendations to remove Reco ransomware and decrypt .reco files.
How to remove Reco Ransomware
First of all, don’t panic. Follow these easy steps below.
1. Start your computer in Safe Mode with networking. To do that, restart your computer before your system starts hit F8 several times. This will Reco Ransomware system from loading and will show Advanced boot options screen. Choose Safe mode with networking option from the options list using up and down arrows on your keyboard and hit Enter.
2. Log in to the system infected with the Reco Ransomware virus. Launch your Internet browser and download a reliable anti-malware program and start a full system scan. Once the scan is complete, review scan results and remove all entries detected.
Recommended Solution:
[TABS_R id=26346]
Restore your files using shadow copies

- Download and run Stellar Data Recovery.
- Select the drive and folder where your files are located and date that you want to restore them from and press Scan.
- Choose all files on folder you want to restore and select Restore.
- Choose export location and view restored files.
Step 2: Remove following files and folders of Reco Ransomware:
Related connections or other entries:
No information
Related files:
No information
How to decrypt files infected by Reco Ransomware?
You can try to use manual methods to restore and decrypt your files.
Decrypt files manually
Restore the system using System Restore

Although the latest versions of Reco Ransomware remove system restore files, this method may help you to partially restore your files. Give it a try and use standard System Restore to revive your data.
- Initiate the search for ‘system restore‘
- Click on the result
- Choose the date before the infection appearance
- Follow the on-screen instructions
Roll the files back to the previous version
Previous versions can be copies of files and folders created by Windows Backup (if it is active) or copies of files and folders created by System Restore. You can use this feature to restore files and folders that you accidentally modified or deleted, or that were damaged. This feature is available in Windows 7 and later versions.

- Right-click the file and choose Properties
- Open the Previous Version tab
- Select the latest version and click Copy
- Click Restore
How to prevent your system from Ransomware?
Make sure your Remote Desktop Protocol (RDP) connection is closed when you don’t use it. Also, we recommend using a strong password for this service. The most efficient way to avoid data lose is of course to make a backup of all important data from your computer.

