How to remove Win32/Genkryptik.Agjs
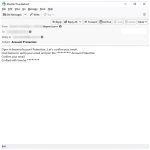
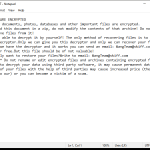
Win32/Genkryptik.Agjs is a type of computer malware that belongs to the Trojan family. Trojans are malicious programs that disguise themselves as legitimate software, trick users into installing them, and then perform harmful actions on the infected computer.
Win32/Genkryptik.Agjs usually infects computers through various means, including:
1. Email attachments: The malware may be distributed through infected email attachments, where users unknowingly download and execute the malicious program by opening the attachment.
2. Software downloads: It can be bundled with freeware or pirated software, which users download from untrusted sources. Once the infected software is installed, the Trojan gains access to the system.
3. Exploiting vulnerabilities: The Trojan can exploit security vulnerabilities in outdated software or operating systems. By exploiting these vulnerabilities, it can execute its code on the infected computer.
4. Drive-by downloads: It may infect a computer when a user visits a compromised website that contains malicious code. The code is automatically downloaded and executed without the user’s knowledge or consent.
Once Win32/Genkryptik.Agjs infects a computer, it can perform various malicious activities, such as:
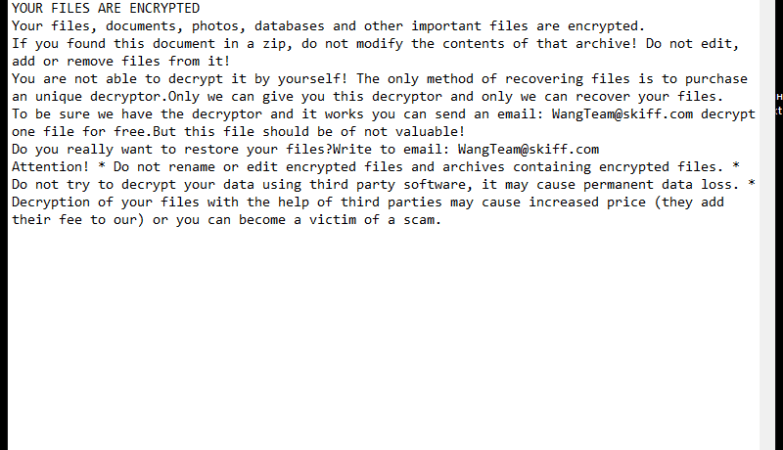
1. Stealing sensitive information: The Trojan may attempt to steal personal data, login credentials, financial information, or other sensitive information stored on the infected computer.
2. Creating backdoors: It can create a “backdoor” on the infected system, allowing unauthorized access to the computer by remote attackers. This can lead to further malware infections or unauthorized control over the compromised system.
3. Modifying system settings: The Trojan may modify system settings, disable security software, or change firewall rules to ensure its persistence and prevent removal.
4. Downloading additional malware: It can download and install other malware onto the infected computer, expanding the scope of the infection and causing further damage.
To protect your computer from Win32/Genkryptik.Agjs and other malware, it is important to have up-to-date antivirus software, regularly update your operating system and software applications, avoid downloading files from untrusted sources, and exercise caution when opening email attachments or visiting unfamiliar websites.