Xam Ransomware is a type of malicious software that encrypts files on a victim’s computer, making them inaccessible until a ransom is paid to the cybercriminals behind the attack. It typically infects computers through malicious email attachments, fake software updates, or through vulnerabilities in outdated software.
Xam Ransomware adds the “.xam” file extension to encrypted files, making them easily identifiable. It uses strong encryption algorithms such as AES or RSA to lock the files, making it nearly impossible to decrypt them without the decryption key.
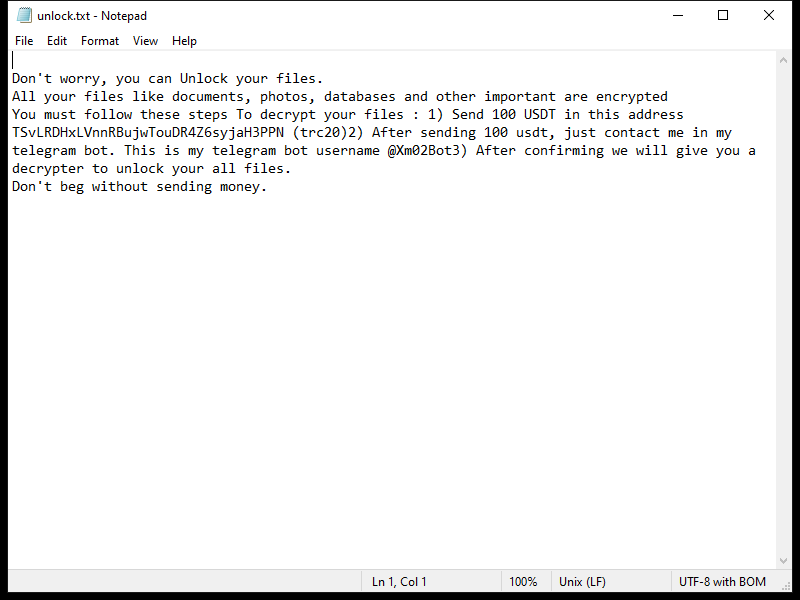
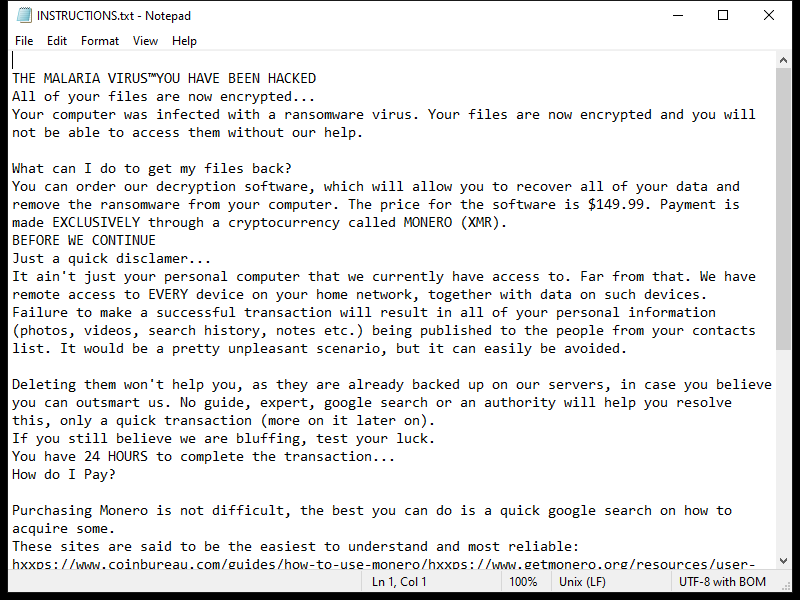
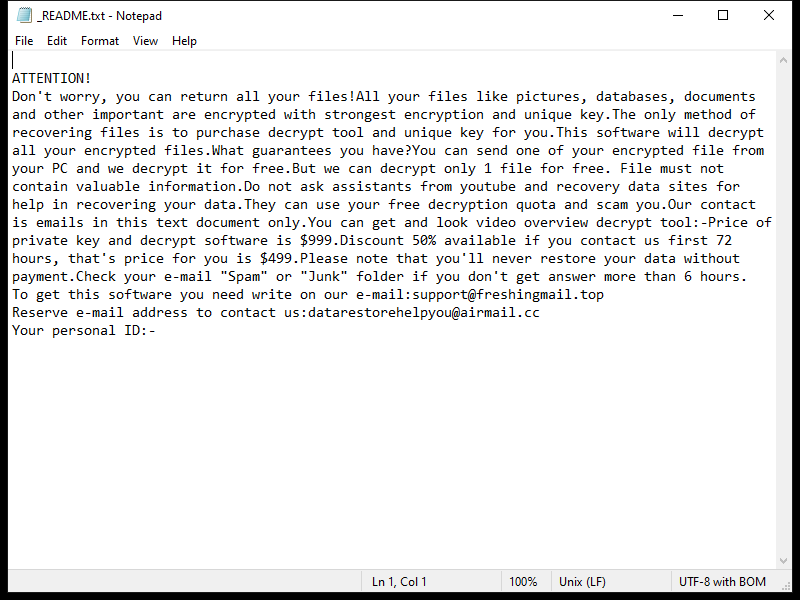
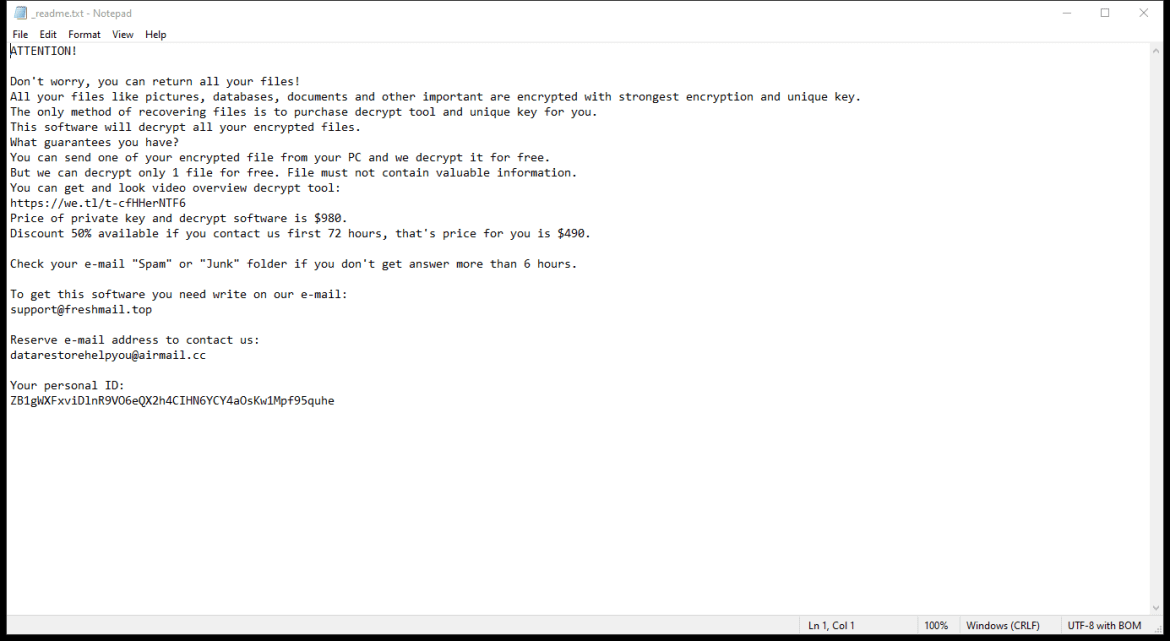
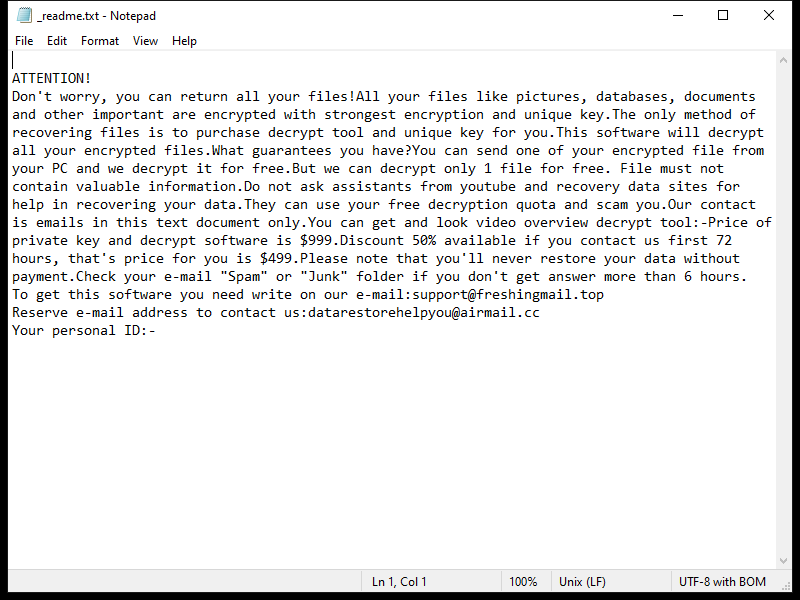
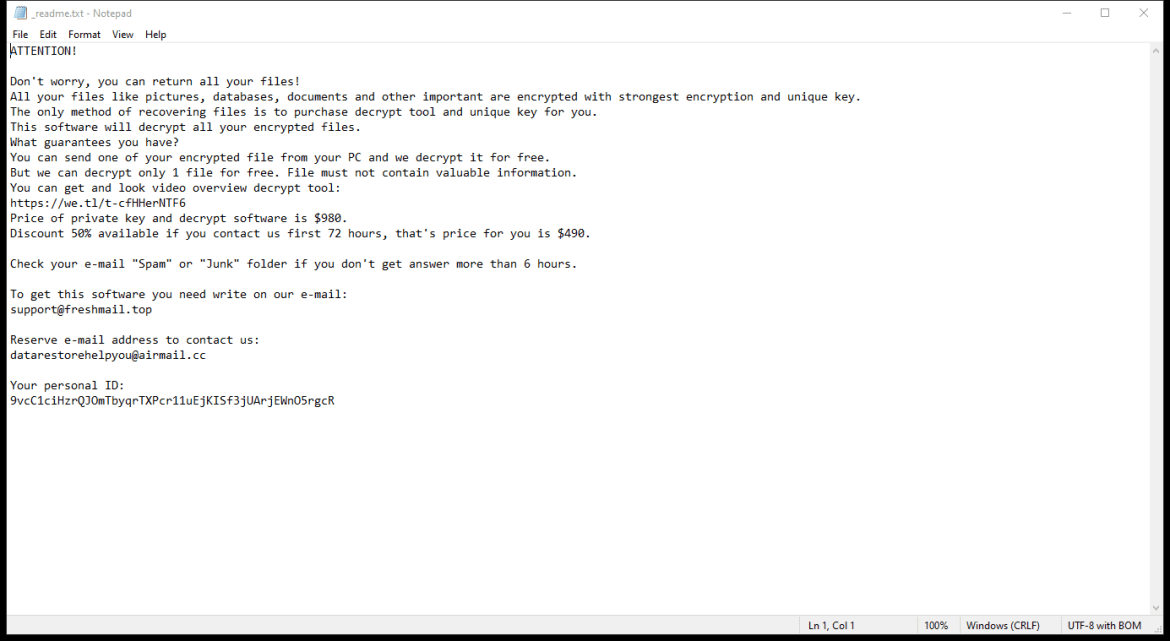
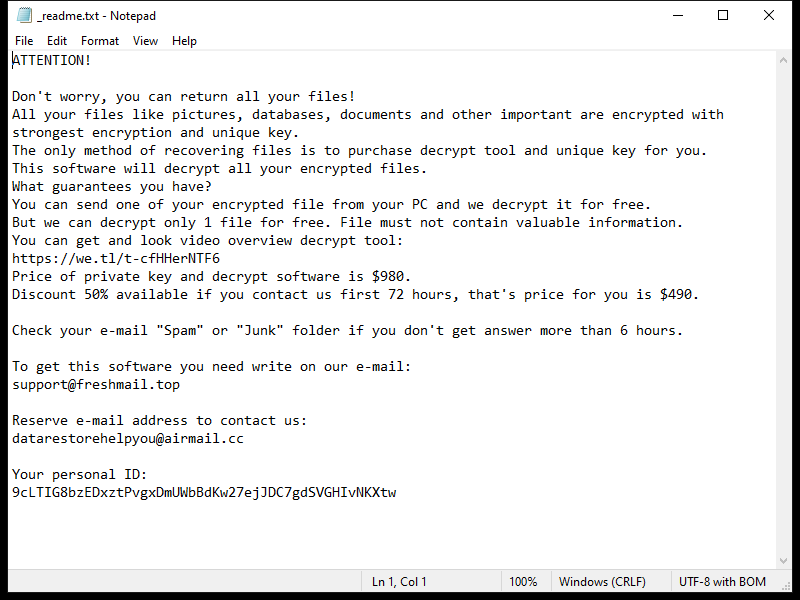
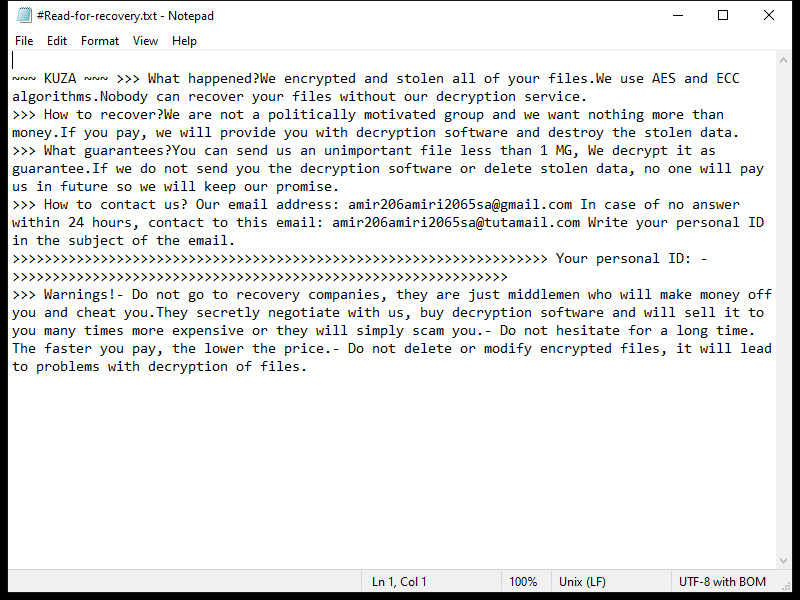
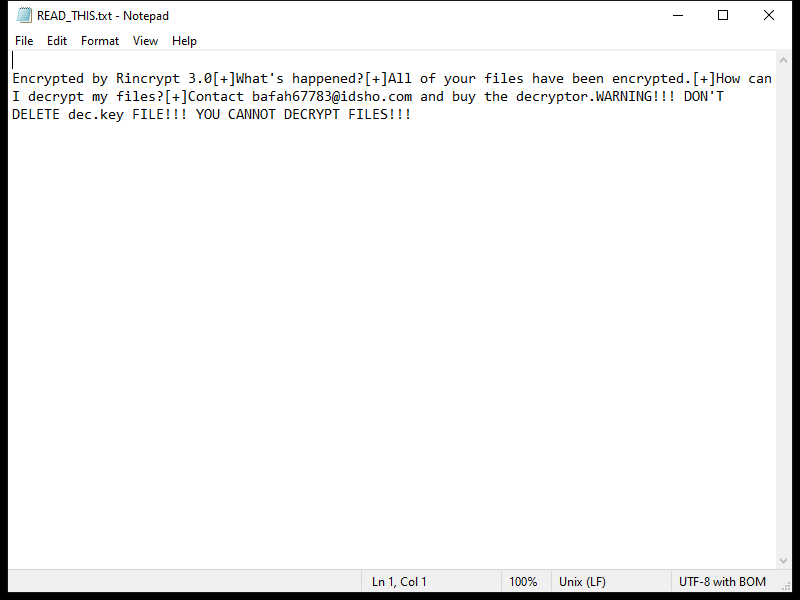
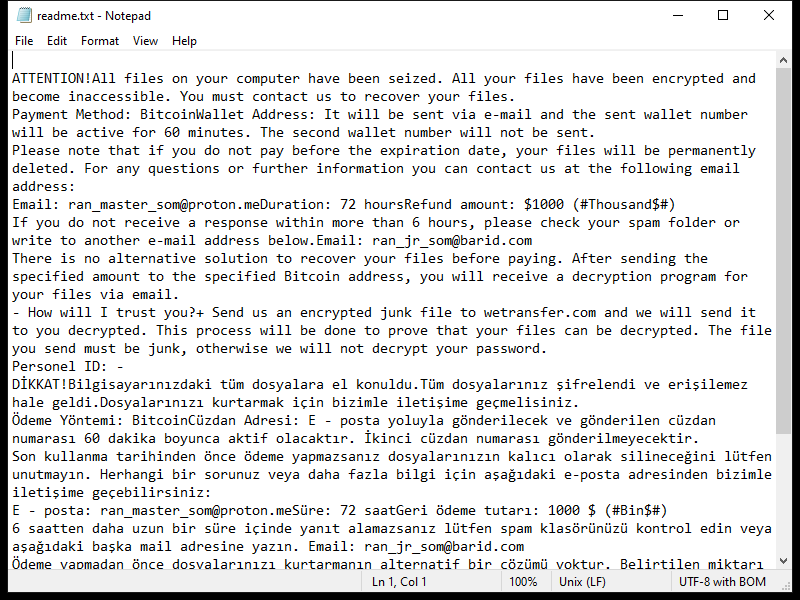
After encrypting the files, Xam Ransomware creates a ransom note typically named “README.txt” or “HOW_TO_DECRYPT.txt” on the desktop or in folders containing encrypted files. The note contains instructions on how to pay the ransom and receive the decryption key.
As of now, there are no decryption tools available for Xam Ransomware. However, victims are advised not to pay the ransom as it does not guarantee the safe return of their files and only encourages cybercriminals to continue their illegal activities.
If you have been affected by Xam Ransomware, the best course of action is to restore your files from a backup if available, or seek help from cybersecurity professionals who may be able to assist in recovering your data.