What is Shadow (Ran_jr_som) Ransomware
Shadow (Ran_jr_som) Ransomware is a type of malicious software that encrypts files on a victim’s computer and demands a ransom for their decryption. It typically infects computers through malicious email attachments, exploit kits, or fake software updates.
When encrypting files, Shadow Ransomware adds the .shadow extension to the filenames, making them inaccessible to the user. It uses strong encryption algorithms such as AES or RSA to lock the files, making decryption without the proper key nearly impossible.
After encrypting the files, Shadow Ransomware creates a ransom note, typically named “README_SHADOW.txt” or similar, which contains instructions on how to pay the ransom to get the decryption key. This note is usually placed on the desktop or in folders containing encrypted files.
At the time of writing, there are no decryption tools available for Shadow Ransomware. However, victims are advised not to pay the ransom as there is no guarantee that the cybercriminals will provide the decryption key. Instead, they should regularly back up their files, update their security software, and seek help from cybersecurity experts to try and recover their files.
You can not trust scammers and pay money without a guarantee of receiving files. The most effective way to get your files back is to remove Shadow (Ran_jr_som) Ransomware to prevent infection. There are 2 options for solving this problem. The first is to use an automatic removal utility that will remove the threat and all instances related to it. Moreover, it will save you time. Or you can use the Manual Removal Guide, but you should know that it might be very difficult to remove Shadow (Ran_jr_som) Ransomware manually without a specialist’s help. If for any reason you need to recover deleted or lost files, then check out our article Top 5 Deleted File Recovery Software
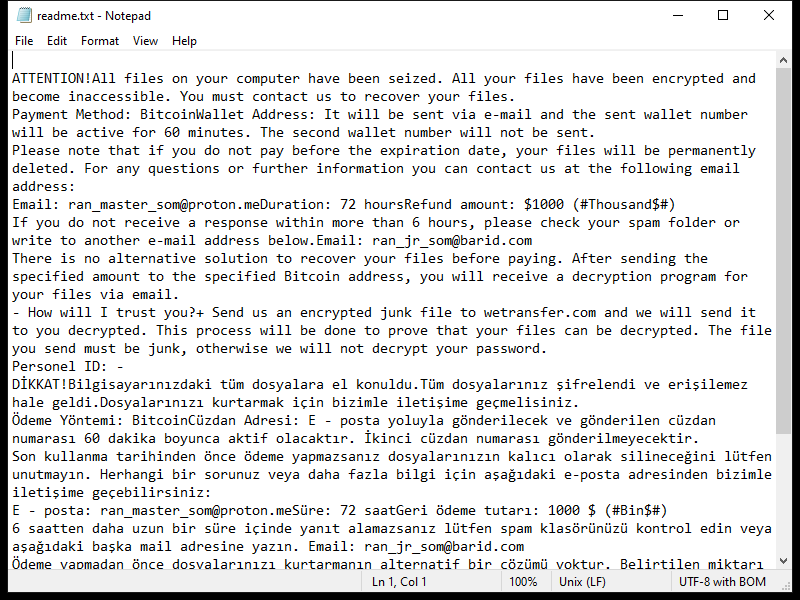
Contents of the ransom note:
ATTENTION!All files on your computer have been seized. All your files have been encrypted and become inaccessible. You must contact us to recover your files.
Payment Method: BitcoinWallet Address: It will be sent via e-mail and the sent wallet number will be active for 60 minutes. The second wallet number will not be sent.
Please note that if you do not pay before the expiration date, your files will be permanently deleted. For any questions or further information you can contact us at the following email address:
Email: ran_master_som@proton.meDuration: 72 hoursRefund amount: $1000 (#Thousand$#)
If you do not receive a response within more than 6 hours, please check your spam folder or write to another e-mail address below.Email: ran_jr_som@barid.com
There is no alternative solution to recover your files before paying. After sending the specified amount to the specified Bitcoin address, you will receive a decryption program for your files via email.
- How will I trust you?+ Send us an encrypted junk file to wetransfer.com and we will send it to you decrypted. This process will be done to prove that your files can be decrypted. The file you send must be junk, otherwise we will not decrypt your password.
Personel ID: -
DİKKAT!Bilgisayarınızdaki tüm dosyalara el konuldu.Tüm dosyalarınız şifrelendi ve erişilemez hale geldi.Dosyalarınızı kurtarmak için bizimle iletişime geçmelisiniz.
Ödeme Yöntemi: BitcoinCüzdan Adresi: E - posta yoluyla gönderilecek ve gönderilen cüzdan numarası 60 dakika boyunca aktif olacaktır. İkinci cüzdan numarası gönderilmeyecektir.
Son kullanma tarihinden önce ödeme yapmazsanız dosyalarınızın kalıcı olarak silineceğini lütfen unutmayın. Herhangi bir sorunuz veya daha fazla bilgi için aşağıdaki e-posta adresinden bizimle iletişime geçebilirsiniz:
E - posta: ran_master_som@proton.meSüre: 72 saatGeri ödeme tutarı: 1000 $ (#Bin$#)
6 saatten daha uzun bir süre içinde yanıt alamazsanız lütfen spam klasörünüzü kontrol edin veya aşağıdaki başka mail adresine yazın. Email: ran_jr_som@barid.com
Ödeme yapmadan önce dosyalarınızı kurtarmanın alternatif bir çözümü yoktur. Belirtilen miktarı belirtilen Bitcoin adresine gönderdikten sonra, e-posta yoluyla dosyalarınız için bir şifre çözme programı alacaksınız.
- Sana nasıl güveneceğim?+ Wetransfer.com'a şifreli bir önemsiz dosya gönderin, biz de size şifresi çözülmüş olarak gönderelim. Bu işlem dosyalarınızın şifresinin çözülebileceğini kanıtlamak için yapılacaktır. Göndereceğiniz dosya önemsiz olmalıdır, aksi takdirde şifrenizin şifresini çözemeyiz.
Personel ID: -
Shadow (Ran_jr_som) Ransomware Removal Guide

Remember that you need to remove Shadow (Ran_jr_som) Ransomware first and foremost to prevent further encryption of your files before the state of your data becomes totally useless. And only after that, you can start recovering your files. Removal must be performed according to the following steps:
Download Shadow (Ran_jr_som) Ransomware Removal Tool
SpyHunter 5 is a powerful malware detection and removal tool developed by EnigmaSoft Limited. It’s designed to provide robust protection against a wide range of malware threats, including viruses, trojans, worms, rootkits, and ransomware. SpyHunter 5 is particularly known for its effectiveness in dealing with complex and evolving malware types that traditional antivirus programs may struggle to detect.
Manual Shadow (Ran_jr_som) Ransomware Removal Guide
Here are step-by-step instructions to remove Shadow (Ran_jr_som) Ransomware from Windows. Follow these steps carefully and remove files and folders belonging to Shadow (Ran_jr_som) Ransomware. Firstly, you need to run the system in a Safe Mode. Then find and remove needed files and folders.
Shadow (Ran_jr_som) Ransomware files:
{randomname}.exe, readme.txt
Clean up hosts file to access security websites
Cleaning up the “hosts” file from unwanted entries involves a few steps. The “hosts” file is a system file used by an operating system to map hostnames to IP addresses. Often, viruses add entries to block popular antivirus websites. It’s important to be cautious when editing this file, as incorrect modifications can cause network issues. Here’s a general guide on how to clean it up:
- Open Notepad as an Administrator:
- Type ‘Notepad’ in the search bar.
- Right-click on the Notepad app and select ‘Run as administrator’.
- Open the Hosts File in Notepad:
- In Notepad, go to File > Open.
- Navigate to
C:\Windows\System32\drivers\etc. - Select “All Files” from the drop-down menu next to the filename text box.
- Open the “hosts” file.
- Edit the File:
- Locate any unwanted entries. These are typically at the bottom of the file.
- Remove or comment them out by adding a
#at the beginning of the line.
- Save Your Changes:
- Go to File > Save.
- Close Notepad.
Check for malicious processes on Windows
Checking for malicious processes in Windows involves a few steps and the use of some tools. While some basic checks can be done manually, for a more thorough examination, specialized software is often required. Here’s a guide to help you get started:
- Task Manager:
- Press
Ctrl + Shift + Escto open Task Manager. - Go to the Processes tab.
- Look for any unusual or unfamiliar processes, especially those using high CPU or memory.
- Right-click on a suspicious process and select Open file location to investigate further.
- Press
- Resource Monitor:
- Access Resource Monitor by typing Resource Monitor in the Start menu search bar.
- Check the Overview or CPU tab for suspicious activities.
Remove unwanted startup entries
- Open System Configuration:
- Press
Windows Key + Rto open the Run dialog box. - Type
msconfigand press Enter. This opens the System Configuration window.
- Press
- Navigate to the Startup Tab:
- In the System Configuration window, go to the Startup tab.
- Note: In Windows 10 and later, you might be redirected to the Task Manager for managing startup items.
- Disable Unwanted Startup Programs:
- If within System Configuration, uncheck the boxes next to the programs you want to disable.
- If in Task Manager, select the program and click Disable.
- Apply Changes and Restart:
- Click OK or Apply to save your changes.
- Restart your computer if prompted.
How to decrypt .shadow files
You can try to restore your files with special tools. You may find more detailed info on data recovery software in this article – recovery software. These programs may help you to restore files that were infected and encrypted by ransomware.
Restore data with Stellar Data Recovery
Stellar Data Recovery is able to find and restore different types of encrypted files, including removed emails.
- Download and install Stellar Data Recovery
- Choose drives and folders with your data, then press Scan.
- Select all the files in a folder, then click on Restore button.
- Manage export location. That’s it!
Restore data with Aiseesoft Data Recovery
Aiseesoft Data Recovery recovers deleted files (like photos, documents, emails, audio, video), and also recovers from a computer, hard drive, flash drive, memory card, digital cameras. Recover from accidental deletion, formatted partition, hard drive problem, RAW hard drive, computer crash. We hope this guide was helpful to you. Feel free to leave a comment and tell us what recovery software was (or wasn’t) effective in your case.
Use Windows Previous Versions or Shadow Explorer to recover .shadow files
Using Windows Previous Versions and Shadow Explorer to restore files is a valuable technique, especially when dealing with accidental deletions or file corruptions. It can also be helpful in case of ransomware infections. Here’s how to use each feature:
Using Windows Previous Versions
- Find the File or Folder:
- Right-click on the file or folder you want to restore.
- Select Properties from the context menu.
- Access Previous Versions:
- In the Properties dialog, go to the Previous Versions tab.
- You’ll see a list of available previous versions from restore points or File History backups.
- Restore the File or Folder:
- Select the version you want to restore.
- Click Restore to overwrite the current version, or Copy to place it in a different location.
Using Shadow Explorer
- Download and Install Shadow Explorer:
- Download Shadow Explorer from its official website.
- Install and open the application.
- Select the Volume and Date:
- At the top of the Shadow Explorer window, select the desired drive (volume).
- Choose the date of the shadow copy you want to explore.
- Navigate and Restore Files:
- Navigate through the file system as in Windows Explorer.
- Right-click on the file or folder you wish to restore.
- Select Export and choose where to save the restored file.
How to prevent ransomware infection?
It is always rewarding to prevent ransomware infection because of the consequences it may bring. There are a lot of difficulties in resolving issues with encoders viruses, that’s why it is very vital to keep a proper and reliable anti-ransomware software on your computer. In case you don’t have any, here you may find some of the best offers in order to protect your PC from disastrous viruses.
SpyHunter is a reliable antimalware removal tool application, that is able to protect your PC and prevent the infection from the start. The program is designed to be user-friendly and multi-functional.
