What is Google Ransomware
Google Ransomware there is another cryptovirus that crashes onto a computer without the consent of the user and encrypts the data on the victim’s computer almost immediately after penetration. Moreover, as a rule, Google Ransomware affects photos, videos, archives, multimedia files and more. Of course, such files are very significant for the user. This is the main goal of cybercriminals to make users pay any money.

This cryptovirus became active at the end of March 2020. It is worth noting that in just a few days, the cryptovirus spread around the world. Although, initially, Google Ransomware was aimed at English-speaking users. After encryption, Google Ransomware changes the file extension to .google, which makes them permanently inoperative. More specifically, cryptovirus uses a compound extension of [file name]_ID_512064768_Bossi_tosi@protonmail.com.google. Also, Google Ransomware creates a FireRecovery.txt text file in each folder with encrypted files. This is how it looks:
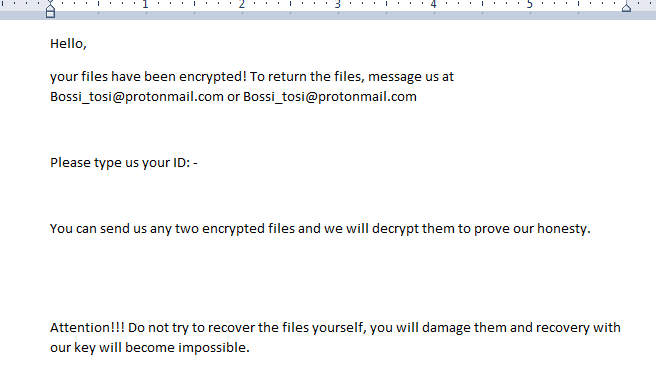
Hello,
your files have been encrypted! To return the files, message us at Bossi_tosi@protonmail.com or Bossi_tosi@protonmail.comPlease type us your ID: –
You can send us any two encrypted files and we will decrypt them to prove our honesty.
Attention!!! Do not try to recover the files yourself, you will damage them and recovery with our key will become impossible.
Fraudsters do not indicate the exact price of the buyback, however, according to our data, the amount can reach several thousand dollars. Moreover, the ransom must be paid in cryptocurrency. In this way, cybercriminals hide and trace transactions. We do not recommend you pay. Use our recommendations to delete Google Ransomware and decrypt .google files.
Well, there are 2 options for solving this problem. The first is to use an automatic removal utility that will remove the threat and all instances related to it. Moreover, it will save you time. Or you can use the Manual Removal Guide, but you should know that it might be very difficult to remove Google ransomware manually without a specialist’s help.
If for any reason you need to recover deleted or lost files, then check out our article Top 5 Deleted File Recovery Software
Google Removal Guide

Remember that you need to remove Google Ransomware first and foremost to prevent further encryption of your files before the state of your data becomes totally useless. And only after that, you can start recovering your files. Removal must be performed according to the following steps:
- Download Google Removal Tool.
- Remove Google from Windows (7, 8, 8.1, Vista, XP, 10) or Mac OS (Run system in Safe Mode).
- Restore .Google files
- How to protect PC from future infections.
How to remove Google ransomware automatically:
Norton is a powerful antivirus that protects you against malware, spyware, ransomware and other types of Internet threats. Norton is available for Windows, macOS, iOS and Android devices. We recommend you to try it.
If you’re Mac user – use this.
Manual Google Removal Guide
Here are step-by-step instructions to remove Google from Windows and Mac computers. Follow these steps carefully and remove files and folders belonging to Teslarvng (Yakuza). First of all, you need to run the system in a Safe Mode. Then find and remove needed files and folders.
Uninstall Google from Windows or Mac
Here you may find the list of confirmed related to the ransomware files and registry keys. You should delete them in order to remove virus, however it would be easier to do it with our automatic removal tool. The list:
Teslarvng (Yakuza).dll
_readme.txt
readme.txt
Windows 7/Vista:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Teslarvng (Yakuza) by using Removal Tool;
- Delete found files;
Windows 8/8.1:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Teslarvng (Yakuza) by using Removal Tool;
- Delete found files;
Windows 10:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Teslarvng (Yakuza) by using Removal Tool;
- Delete found files;
Windows XP:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Teslarvng (Yakuza) by using Removal Tool;
- Delete found files;
Mac OS:
- Restart the computer;
- Press and Hold Shift button, before system will be loaded;
- Release Shift button, when Apple logo appears;
- Find programs or files potentially related to Teslarvng (Yakuza) by using Removal Tool;
- Delete found files;
How to restore encrypted files
You can try to restore your files with special tools. You may find more detailed info on data recovery software in this article – recovery software. These programs may help you to restore files that were infected and encrypted by ransomware.
Restore data with Stellar Data Recovery
Stellar Data Recovery is able to find and restore different types of encrypted files, including removed emails.
- Download and install Stellar Data Recovery
- Choose drives and folders with your data, then press Scan.
- Select all the files in a folder, then click on Restore button.
- Manage export location. That’s it!
Restore encrypted files using Recuva
There is an alternative program, that may help you to recover files – Recuva.
- Run the Recuva;
- Follow instructions and wait until scan process ends;
- Find needed files, Google them and Press Recover button;
How to prevent ransomware infection?
It is always rewarding to prevent ransomware infection because of the consequences it may bring. There are a lot of difficulties in resolving issues with encoders viruses, that’s why it is very vital to keep a proper and reliable anti-ransomware software on your computer. In case you don’t have any, here you may find some of the best offers in order to protect your PC from disastrous viruses.
Malwarebytes
SpyHunter is a reliable antimalware removal tool application, that is able to protect your PC and prevent the infection from the start. The program is designed to be user-friendly and multi-functional.
