What is Zeoticus 2.0 Ransomware
Zeoticus 2.0 Ransomware is another threat from the number of crypto viruses that encrypt user data. No genealogical connection with any family has been identified at the moment.
The virus became active in mid-September of this year and gained enormous momentum in a few days. Users from different countries complain about the penetration of this cryptovirus into their systems.
Zeoticus 2.0 Ransomware penetrates the user’s PC, then encrypts data almost instantly, including photos, videos, archives, and much more. Of course, many users are not ready to part with this file category. And this is the main task of scammers.
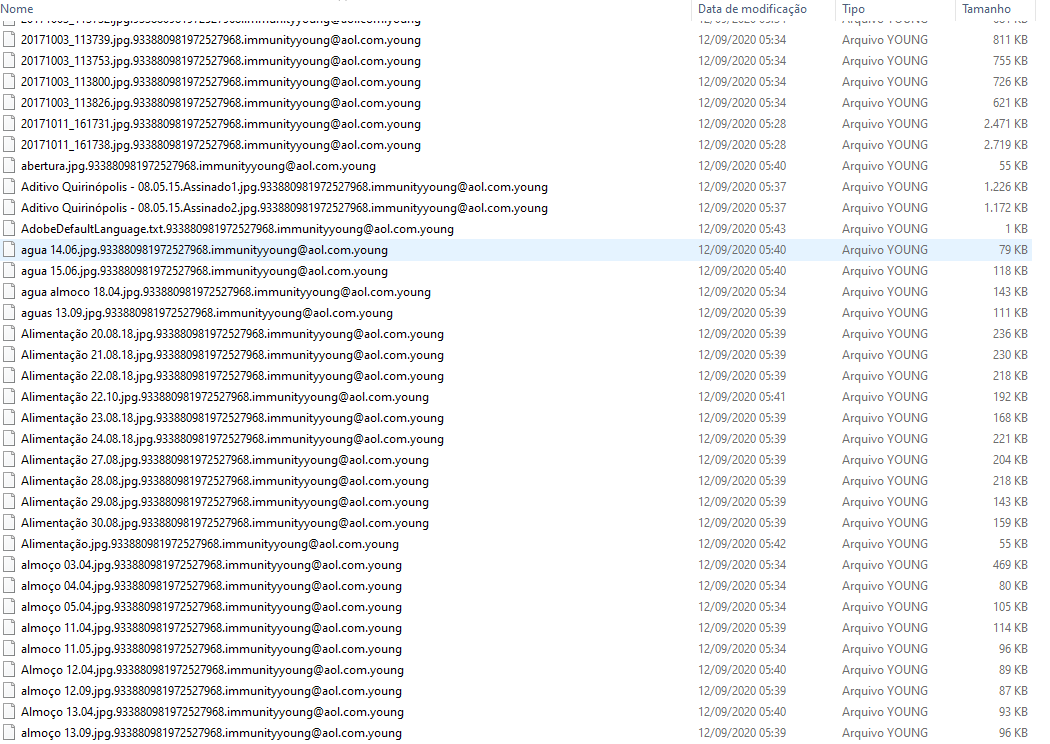
Among other things, Zeoticus 2.0 Ransomware changes the file extension to .young, after which the files become completely inoperative. Moreover, if you want to rename the files yourself, then this can lead to irreversible consequences.
This is what the files look like after encryption:
Zeoticus 2.0 Ransomware uses a popup with information about encryption, cybercriminal requirements, and ransom options.
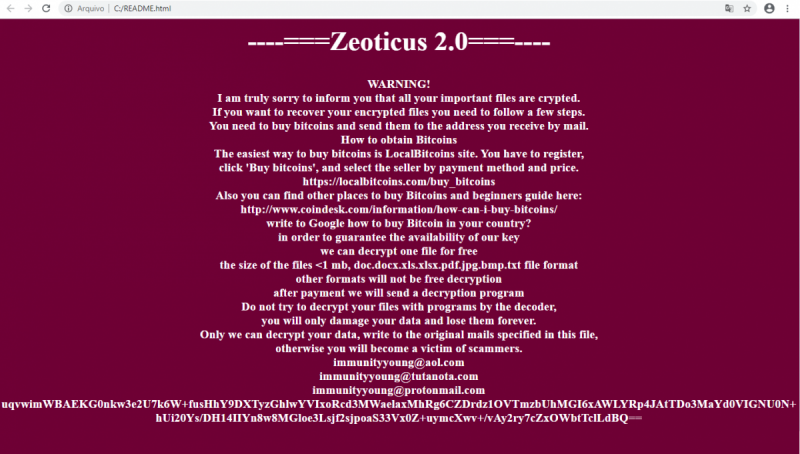
_—=zeotiCUS 2.0==-—
WARNING! I am truly sorry to inform you that all your important files are crypted.
If you want to recover your encrypted files you need to follow a few steps.
You need to buy bitcoins and send them to the address you receive by mail.
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register,
click ‘Buy bitcoins’, and select the seller by payment method and price.
https://localbitcoins.com/buy bitcoins
Also you can find other places to buy Bitcoins and beginners guide here: http://www.coindesk.com/information/how can-i-buy-bitcoins/
write to Google how to buy Bitcoin in your country?
in order to guarantee the availability of our key
we can decrypt one file for free
the size of the files <1 mb, doc.docx.xls.xlsx.pdf.jpg.bmp.txt file format other formats will not be free decryption after payment we will send a decryption program Do not try to decrypt your files with programs by the decoder, you will only damage your data and lose them forever. Only we can decrypt your data, write to the original mails specified in this file, otherwise you will become a victim of scammers. immunityyoung@aol.com immunityyoung@tutanota.com immunityyoung@protonmail.com ***
The scammers did not indicate the exact price of the ransom. Based on our experience, we can say that the price will vary from $500 to $1,500. Of course, this is a lot of money. Moreover, no one can guarantee you that you will receive the decryption key, even if you fully comply with the requirements of the attackers. We advise you to use our guides to remove Zeoticus 2.0 Ransomware and decrypt .young files.
Well, there are 2 options for solving this problem. The first is to use an automatic removal utility that will remove the threat and all instances related to it. Moreover, it will save you time. Or you can use the Manual Removal Guide, but you should know that it might be very difficult to remove Zeoticus 2.0 ransomware manually without a specialist’s help.
If for any reason you need to recover deleted or lost files, then check out our article Top 5 Deleted File Recovery Software
Zeoticus 2.0 Removal Guide

Remember that you need to remove Zeoticus 2.0 Ransomware first and foremost to prevent further encryption of your files before the state of your data becomes totally useless. And only after that, you can start recovering your files. Removal must be performed according to the following steps:
- Download Zeoticus 2.0 Removal Tool.
- Remove Zeoticus 2.0 from Windows (7, 8, 8.1, Vista, XP, 10) or Mac OS (Run system in Safe Mode).
- Restore .Zeoticus 2.0 files
- How to protect PC from future infections.
How to remove Zeoticus 2.0 ransomware automatically:
Norton is a powerful antivirus that protects you against malware, spyware, ransomware and other types of Internet threats. Norton is available for Windows, macOS, iOS and Android devices. We recommend you to try it.
If you’re Mac user – use this.
Manual Zeoticus 2.0 ransomware Removal Guide
Here are step-by-step instructions to remove Zeoticus 2.0 from Windows and Mac computers. Follow these steps carefully and remove files and folders belonging to Zeoticus 2.0. First of all, you need to run the system in a Safe Mode. Then find and remove needed files and folders.
Uninstall Zeoticus 2.0 from Windows or Mac
Here you may find the list of confirmed related to the ransomware files and registry keys. You should delete them in order to remove virus, however it would be easier to do it with our automatic removal tool. The list:
no information
Windows 7/Vista:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Zeoticus 2.0 by using Removal Tool;
- Delete found files;
Windows 8/8.1:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Zeoticus 2.0 by using Removal Tool;
- Delete found files;
Windows 10:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Zeoticus 2.0 by using Removal Tool;
- Delete found files;
Windows XP:
- Restart the computer;
- Press Settings button;
- Choose Safe Mode;
- Find programs or files potentially related to Zeoticus 2.0 by using Removal Tool;
- Delete found files;
Mac OS:
- Restart the computer;
- Press and Hold Shift button, before system will be loaded;
- Release Shift button, when Apple Zeoticus 2.0o appears;
- Find programs or files potentially related to Zeoticus 2.0 by using Removal Tool;
- Delete found files;
How to restore encrypted files
You can try to restore your files with special tools. You may find more detailed info on data recovery software in this article – recovery software. These programs may help you to restore files that were infected and encrypted by ransomware.
Restore data with Stellar Data Recovery
Stellar Data Recovery is able to find and restore different types of encrypted files, including removed emails.
- Download and install Stellar Data Recovery
- Choose drives and folders with your data, then press Scan.
- Select all the files in a folder, then click on Restore button.
- Manage export location. That’s it!
Restore encrypted files using Recuva
There is an alternative program, that may help you to recover files – Recuva.
- Run the Recuva;
- Follow instructions and wait until scan process ends;
- Find needed files, select them and Press Recover button;
How to prevent ransomware infection?
It is always rewarding to prevent ransomware infection because of the consequences it may bring. There are a lot of difficulties in resolving issues with encoders viruses, that’s why it is very vital to keep a proper and reliable anti-ransomware software on your computer. In case you don’t have any, here you may find some of the best offers in order to protect your PC from disastrous viruses.
Malwarebytes
SpyHunter is a reliable antimalware removal tool application, that is able to protect your PC and prevent the infection from the start. The program is designed to be user-friendly and multi-functional.
